Table of Contents
In the vast expanse of the internet, where our online lives are built on a network of information, there’s always a risk of someone trying to steal our identity. As people who use the internet, our online identities are both our most valuable asset and our most vulnerable point of entry for malicious actors. However, even within this risky setting, there’s still hope for safety, with identity threat detection. Let’s explore how important these tools are and how they protect us in the face of cyber adversity.
What is Identity Theft?
One word to describe identity theft would be “impersonating.” It is a crime involving the use of personal or financial information belonging to another individual to commit fraud, such as making unauthorized transactions or purchases. Identity threat comprises of situations where an individual’s personal or sensitive information is jeopardized, misused, or stolen by malicious entities. This includes unauthorized access to personal accounts, instances of identity theft, phishing scams, or other cyber-attacks designed to exploit vulnerabilities in an individual’s digital identity. Identity threats pose a significant risk to individuals’ privacy, financial security, and overall well-being in an increasingly interconnected and digital world.
Types of Identity Theft
Financial Identity Theft
Financial identity theft occurs when someone uses another person’s identity or information to obtain credit, goods, services, or benefits. This is the most common form of identity theft.
Social Security Identity Theft
If identity thieves obtain your Social Security number, they can use it to apply for credit cards and loans and then not pay outstanding balances. Fraudsters can also use your number to receive medical, disability, and other benefits.
Medical Identity Theft
In medical identity theft, someone poses as another person to obtain free medical care.
Synthetic Identity Theft
Synthetic identity theft is a type of fraud in which a criminal combines real (usually stolen) and fake information to create a new identity. This new identity is used to open fraudulent accounts and make fraudulent purchases. Synthetic identity theft allows the criminal to steal money from credit card companies and lenders who extend their credit based on the fake identity.
Child Identity Theft
Child identity theft involves using a child’s identity for various forms of personal gain. This is common, as children typically do not have the capability to take steps to create obstacles for the perpetrator. The fraudster may use the child’s name and Social Security number to obtain a residence, find employment, obtain loans, or avoid arrest on outstanding warrants. Often, the victim is a family member, the child of a friend, or someone else close to the perpetrator. Some people even steal the personal information of deceased loved ones.
Tax Identity Theft
Tax identity theft occurs when someone uses your personal information, including your Social Security number, to file a bogus state or federal tax return in your name and collect a refund.
Criminal Identity Theft
In criminal identity theft, a criminal poses as another person during an arrest to try to avoid a summons, prevent the discovery of a warrant issued in their real name, or avoid an arrest or conviction record.
Identity Threat Detection
Introduction
With the internet intersecting with every aspect of our lives, the concept of identity threat detection becomes increasingly important. As we use many online platforms, our online identities are like keys to using many services, from banking and shopping to social media and work. But with this increased connection comes the danger of our online identities being attacked by malicious actors seeking to exploit vulnerabilities for their gain.
Identity threat detection stands as a pivotal defense mechanism in this digital battleground, employing advanced technologies and methodologies to safeguard our personal and sensitive information from unauthorized access and misuse. By actively monitoring online activities, analyzing patterns, and identifying anomalies, identity threat detection systems serve as the guardians of our digital identities, alerting us to potential risks and enabling timely intervention to mitigate threats before they escalate.
In this era of heightened cybersecurity concerns, understanding the fundamental concepts of identity threat detection is essential for individuals and organizations alike. From its role in proactively identifying suspicious behavior to its contribution to enhancing overall online security posture, the significance of identity threat detection cannot be overstated.
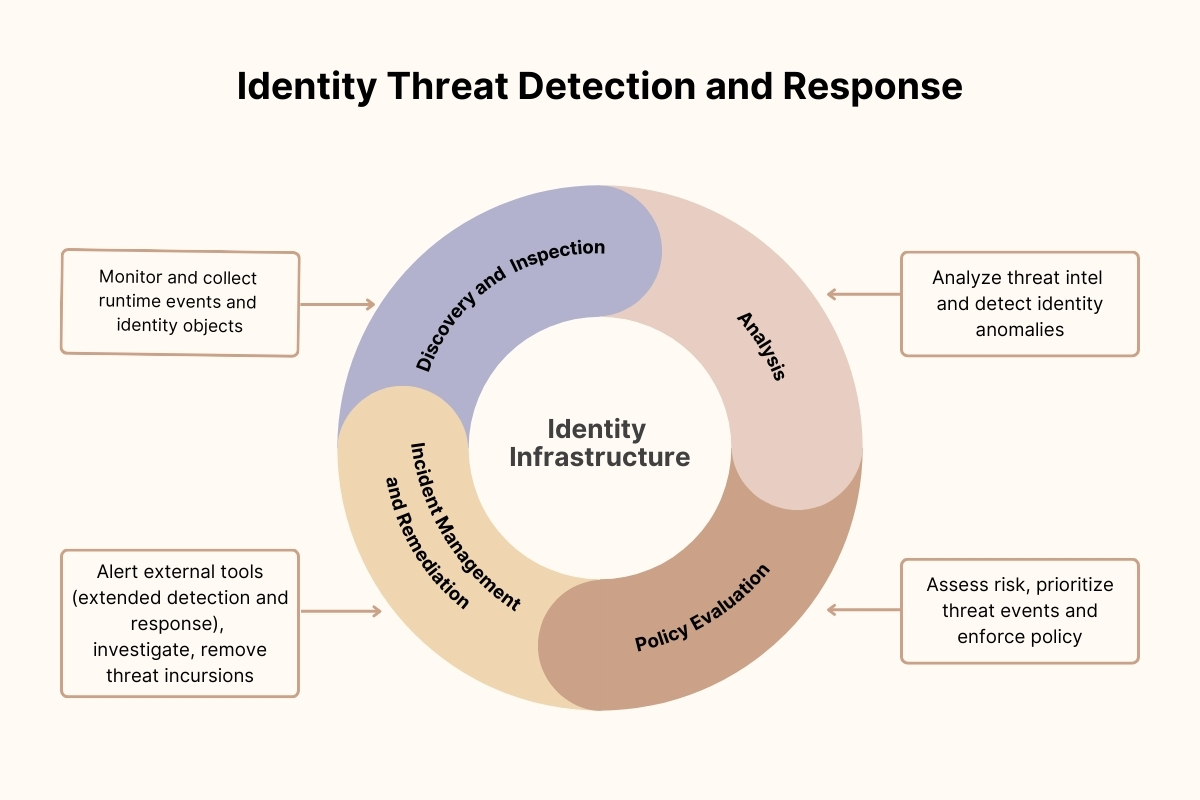
Identity Threat Detection and Response (ITDR) System
Identity Threat Detection and Response (ITDR) represents a distinct category within cybersecurity solutions, standing alongside established counterparts such as endpoint detection and response (EDR), extended detection and response (XDR), network detection and response (NDR), and privileged access management (PAM) systems. While each of these solutions plays a vital role in strengthening organizational security, the emergence of ITDR signifies a significant departure from traditional offerings, particularly in its focus on safeguarding identities and identity systems.
The necessity for dedicated ITDR systems arises from the understanding that identities require specialized attention within the cybersecurity landscape. A comprehensive ITDR system encompasses a range of vulnerability and threat detection, and response capabilities tailored specifically to protect identities and identity-related assets.
Outlined below are key identity-centric security controls that an effective ITDR system should support:
- Configuration, Policy, and Identity Data Analysis: Assessing the security posture of an organization’s Active Directory environment through meticulous analysis of configuration settings, policies, and identity-related data.
- Attack Path Management and Impact Analysis: Identifying potential attack paths targeting identity systems and conducting impact analyses to gauge the severity of potential security breaches.
- Risk Scoring and Remediation Prioritization: Assigning risk scores to identity-related vulnerabilities and prioritizing remediation efforts based on the level of risk posed to the organization.
- Real-Time Monitoring of Runtime Behaviors: Continuously monitoring runtime behaviors for identity-centric indicators of compromise, enabling swift detection and response to potential security incidents.
- Machine Learning or Analytics: Leveraging advanced analytics and machine learning algorithms to detect abnormal behaviors or events indicative of identity-related threats.
- Automated Remediation and Incident Response: Implementing automated remediation processes and incident response workflows to address identity-related security incidents promptly.
- Dashboards, Alerts, Reports, Search, and Incident Management: Providing intuitive dashboards, alerts, reports, and search functionalities to facilitate effective incident management and response.
- Integration with Security Information and Event Management (SIEM), XDR, and SOAR Tools: Seamless integration with SIEM, XDR, and security orchestration automation and response (SOAR) tools to enhance visibility and orchestration capabilities across security operations.
- Integration with Multifactor Authentication (MFA) Solutions: Collaborating with MFA solutions to deliver step-up authentication in response to identity-related risk events, strengthening access controls.
- Integration with Privileged Access Management (PAM) Tools: Integrating with PAM tools to identify gaps in coverage for highly privileged accounts and enforce robust access controls.
- Risk Signal Sharing: Sharing risk signals with suite providers and third-party tools to facilitate informed risk management decisions and enhance overall security posture.
The rise of ITDR underscores the critical importance of managing and controlling identities with the same rigor applied to other aspects of cybersecurity. As identities increasingly become the primary target for cyber-attacks, organizations must prioritize the implementation of comprehensive ITDR solutions to mitigate identity-related risks effectively.
ITDR Insights
The Gartner report “Enhance Your Cyberattack Preparedness with Identity Threat Detection and Response” in 2022 highlights key features shaping the cybersecurity landscape. Here are some key insights that highlights the growing significance of Identity Threat Detection and Response (ITDR):
- The COVID-19 pandemic has heightened remote work dynamics making identity infrastructure a prime focal point for cyber adversaries. Organizations that rely on identity systems for remote collaboration and customer access are especially at risk. They need robust ITDR measures to counter emerging threats effectively.
- The pervasive adoption of cloud computing and remote work support has spotlighted vulnerabilities inherent within identity infrastructure. Exploitable misconfigurations and weaknesses in identity systems have created a surge in ransomware-related incidents, compelling organizations to prioritize proactive identity security measures.
- The phased rollout of identity systems often exposes organizations to vulnerabilities during implementation stages. Cyber attackers adeptly exploit disparities between identity and security systems, capitalizing on the dynamic nature of identities to evade detection. Cumbersome manual auditing processes heighten these challenges, necessitating streamlined ITDR strategies.
- Modern identity threats go beyond conventional IAM controls, warranting a paradigm shift towards proactive detection and response mechanisms. ITDR ascends as a critical cybersecurity priority, with organizations acknowledging the imperative of fortifying identities to mitigate evolving cyber risks effectively.
In summation, the Gartner report underscores the pivotal role of ITDR in navigating evolving cybersecurity terrains. Armed with insights into emerging trends, organizations can bolster their cybersecurity postures and safeguard invaluable assets and data against an ever-evolving threat landscape.
Proactive measures to safeguard your personal information
- Safely store documents containing personal details, such as financial records, Social Security, Medicare, and credit cards, both at home and in the workplace.
- Exercise caution in what you carry. Reserve the carrying of your social security card and Medicare card for instances when their use is specifically required.
- Refrain from divulging personal, financial, or health-related information over the phone, via mail, or online unless you have established a trusted relationship with the recipient and initiated the contact.
- Scrutinize your credit card receipts, ensuring they do not display your complete account number.
- Utilize a single credit card exclusively for online purchases, refraining from using a debit card for such transactions.
- Promptly retrieve your mail and utilize a secure mailbox to prevent unauthorized access to sensitive correspondence.
- Employ a “cross-cut” shredder to securely dispose of receipts, credit offers, loan applications, insurance forms, bank statements, and similar documents once they are no longer needed.
- Employ unique and robust passwords for each of your accounts and take measures to safeguard them effectively.
- Before selling, giving away, or disposing of a laptop, computer, or mobile device, ensure all personal information stored on the device is thoroughly erased.
In summary, the significance of identity threat detection in today’s digital realm cannot be understated. With cyber threats continuously evolving and targeting identities as the primary attack vector, the implementation of robust identity threat detection measures is paramount. By actively monitoring online activities, analyzing patterns, and detecting anomalies, identity threat detection serves as a crucial defense mechanism against unauthorized access, fraudulent activities, and data breaches.
For both individuals and organizations, investing in identity threat detection offers numerous benefits. These include early detection of suspicious activities, enabling swift response and mitigation of potential threats, as well as enhanced protection of sensitive personal and organizational information. Moreover, the adoption of identity threat detection contributes to a strengthened cybersecurity posture through proactive identification and remediation of identity-related risks. Additionally, it ensures compliance with regulatory requirements and industry standards concerning data protection and security.
Therefore, it is strongly encouraged that individuals and organizations prioritize the implementation of identity threat detection solutions. By taking proactive steps to safeguard identities and identity systems, we can collectively bolster online security and effectively mitigate the risks posed by evolving cyber threats.

