Telemetry: Revolutionizing Cybersecurity with Real-Time Insights
Table of Contents
In today’s interconnected digital landscape, the importance of cybersecurity cannot be undervalued. Organizations face increasingly sophisticated cyber threats. The need for proactive, data-driven approaches to detect, prevent, and respond to security incidents becomes important and vital. Among the arsenal of cybersecurity tools and methodologies, telemetry emerges as a pivotal component, revolutionizing the way security professionals safeguard critical assets and networks.
What is “Telemetry” in Cyber security?
Telemetry, in the context of cybersecurity, refers to the automated collection, analysis, and transmission of real-time data from various sources across an organization’s IT infrastructure. It encompasses a wide array of information, including network traffic, system logs, endpoint activities, user behaviors, and application performance metrics. This wealth of data serves as a treasure trove for security analysts, enabling them to gain comprehensive visibility into the organization’s digital ecosystem.
At the heart of telemetry’s significance lies its role in threat detection and prevention. By continuously monitoring and analyzing vast streams of data, telemetry allows for the identification of abnormal patterns, deviations from established norms, and potential security breaches. Anomaly detection algorithms, powered by telemetry data, raise immediate red flags upon detecting suspicious activities, facilitating swift responses to mitigate threats before they escalate.
There are many areas where telemetry can contribute to organizations cyber security landscape.
- Threat Detection and Prevention
- Incident Response and Investigation
- Enhanced Security Operations
- Compliance and Risk Management
- Decision Making and Strategy
Threat Detection and Prevention:
Anomaly Detection: Telemetry data helps in detecting abnormal behavior or deviations from normal patterns within the network or systems. Unusual traffic, unexpected access attempts, or deviations in system behavior can be detected and investigated for potential threats.
Intrusion Detection: Continuous monitoring through telemetry aids in identifying potential intrusion attempts, such as unauthorized access, malware activities, or other security breaches.
Incident Response and Investigation:
Forensic Analysis: Telemetry data serves as a critical source of information during incident response and forensic investigations. It provides detailed logs and historical data that can help in understanding the timeline of events leading up to a security incident.
Threat Hunting: Security teams use telemetry to proactively search for signs of potential threats or vulnerabilities within the network. It involves analyzing historical data to uncover hidden threats or vulnerabilities that may not be immediately apparent.
Enhanced Security Operations:
Visibility and Monitoring: Telemetry offers visibility into the entire network infrastructure, including endpoints, servers, applications, and cloud environments. It allows security teams to monitor and assess the security posture in real-time.
Performance Monitoring: Telemetry data not only helps in identifying security threats but also aids in monitoring system performance, identifying bottlenecks, and optimizing resource allocation.
Compliance and Risk Management:
Compliance Monitoring: Telemetry data assists in maintaining compliance with regulatory standards by providing evidence of security controls and activities. It helps organizations demonstrate adherence to security standards and regulations.
Risk Assessment: Analyzing telemetry data allows organizations to assess risks and vulnerabilities accurately. It helps in prioritizing security measures and implementing controls to mitigate potential risks.
Decision Making and Strategy:
Data-Driven Insights: Telemetry generates data-driven insights that aid in making informed decisions regarding cybersecurity strategies, resource allocation, and future investments in security measures.
Continuous Improvement: Leveraging telemetry data enables organizations to continuously improve their security posture by identifying weaknesses, fine-tuning security controls, and adapting to emerging threats and attack vectors.
CrowdStrike: Detections and Tainted Telemetry are Required for an Effective EDR Solution
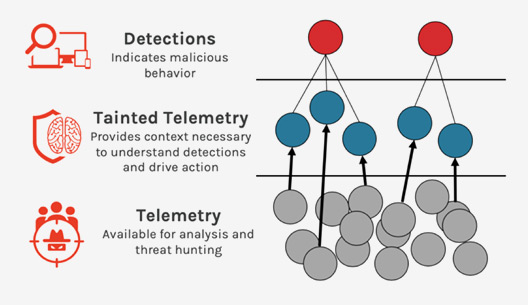
CrowdStrike Falcon® continuously collects comprehensive telemetry, even when malicious or suspicious activity is not being detected on the endpoint. This telemetry includes hundreds of different types of activity such as process creation, HTTP connections, service creation, logins, and many other event types. The CrowdStrike® Falcon® platform makes extensive use of this concept to streamline analysis. Falcon automatically surfaces for the analyst all existing telemetry that is connected to malicious detections. Tainted telemetry allows analysts to understand more threats faster than they could with a less-capable EDR solution.
Cybereason: XDR Performance based on real-time telemetry
AI-driven Cybereason XDR can help organizations embrace an operation-centric approach to security. Cybereason understands that they’re at their best when they’re combined with Indicators of Behavior (IOBs) Organizations can use these subtle signs of compromise to defend themselves against threats—even if someone has never seen them before.
In conclusion, the significance of telemetry in cybersecurity cannot be overstated. Its role in proactive threat detection, incident response, compliance adherence, and data-driven decision-making positions it as an indispensable tool in the arsenal of cybersecurity measures. As organizations navigate the complexities of the digital realm, harnessing the power of telemetry emerges as a linchpin in safeguarding critical assets, mitigating risks, and fortifying defenses against evolving cyber threats.

